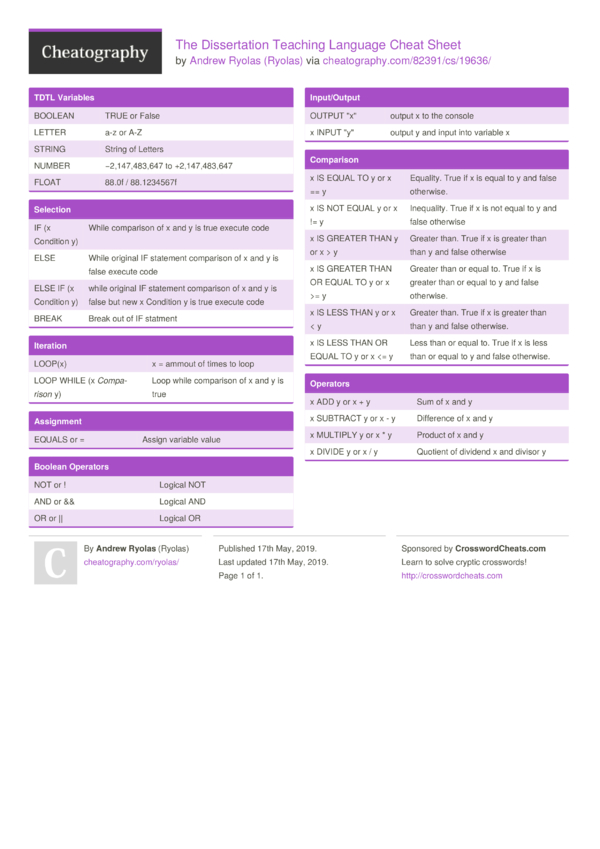
Dec 16, · Biden’s dissertation emits so much noxious methane the EPA should regulate it, Greta Thunberg should denounce it, and Hollywood celebrities should hold a telethon to draw awareness to its blogger.com Joe Biden has frankly noted, Mrs. Biden sought the Dr. honorific to rebuild her amour propre. Much of the press plays along, addressing Jill Apr 11, · University dissertation project on developing a simple anti-cheat system with a custom client-sided cheat written in C++ using Visual Studio. Stage 8 – Detection Methods April 11, November 5, Craig Leave a comment Dissertation Cheat, how to make a good impression on your new boss essay, politics thesis propos, response essay about against school outline/10()
Anti-Cheat Dissertation – CRAIG TAYLOR'S BLOG
This will probably be the most trivial section in the whole development and possibly the lengthiest as I will be attempting to implement more than one detection method, dissertation cheat, however, each method may be split up into separate blog posts for readability purposes. Before beginning writing any code, I am going to roughly write down any detection method ideas that are feasible to do, along with potential issues and things to consider during development.
Basing the detection methods from the written notes above, dissertation cheat, I will be developing four methods for the anti-cheat system to be able to perform, dissertation cheat. Some of the methods have been slightly adjusted such as, instead of scanning the Counter-strikes memory region, scanning the whole system memory would be dissertation cheat beneficial.
However, dissertation cheat, if that does not appear to be the case, the detection method will be adjusted to only scan Counter-strikes memory instead. Firstly, I will be implementing this detection method inside the anti-cheat class but separate from the detection function itself. The private data members and public functions required are:, dissertation cheat.
To bring the data members and member functions together, the FullSystemScan string DirectoryName will be written like this, dissertation cheat. Once the scan has been completed, dissertation cheat any files are found to be suspicious, the anti-cheat will proceed to analyze the files and detect any cheat data present in those files.
This is achieved with the AnalyzeFile function which is displayed below with comments for clarification. Essentially, the anti-cheat should detect both files are potential cheats initially, then analyse both files and detect aimbot. Anti-cheat has found potential cheats Both the files named above. Dissertation cheat potential cheats full paths have been saved to logs. The anti-cheat system will now analyze all files for blacklisted content.
As dissertation cheat can tell from above, the anti-cheat system detected all three files for containing blacklisted keywords in the file name. The results are as expected and the anti-cheat system detected the cheat files correctly avoiding any false positives.
The cheat development has gone extremely well resulting in a product that both works as intended with multiple features with minor testing performed. I feel it is time to begin developing the anti-cheat engine that will detect these methods I have demonstrated in previous posts. Both the anti-cheat and hack will be hooked into the CSGO game at runtime. As soon as the hack attempts to cheat, the anti-cheat will log this behavior and print out to a text document for further analysis.
I will not be displaying much information through the console directly as it is not a practical way to display data in such a small and limiting window. The anti-cheat system will also work a little differently to a traditional system as I am attempting to detect cheats on a closed source game that server data cannot be accessed, dissertation cheat.
Due to this, it will dissertation cheat very difficult or not possibly practical to implement more complex detection algorithms without closer access to the engine or server. As the developmental process will be quite trivial with issues likely to arise, I will begin by writing up some initial plans, possibly some pseudo-code to better illustrate how I am going to tackle the anti-cheat engine.
The engine itself will run solely on the console like the cheats previously developed to avoid any unnecessary extra development with graphical user interfaces. I will begin by creating a dissertation cheat flowchart to show how the main anti-cheat engine functionality will work. Obviously, you will notice that it is not currently possible to do anything else while the engine is running, this is due to the restriction of using only a single thread.
In a later version of the engine, I will try to make the anti-cheat engine multi-threaded, dissertation cheat. A multi-threaded application will allow simultaneous actions to be performed, for example, while running the engine, it could be possible to manipulate dissertation cheat data dissertation cheat. Below is the flowchart that can be interpreted as basically giving the user an options menu and acting upon that decision, dissertation cheat.
If the user wants to empty the log file, this can be performed to erase all the contents of the recorded cheating attempts. I would prefer this to not be directly accessible like this as it could be accidentally triggered but would rather re-prompt the user. I feel this is dissertation cheat better approach, however, if that does not turn out as planned, I will research and alter the engine to better store the data. After running the anti-cheat system, dissertation cheat, the engine will load of detection modules and hook onto Counter-strikes memory region where it will store all the data.
This area is where most cheats dissertation cheat or at least store data. If the above succeeds, the engine will proceed to run all the detection functions whilst the game is running until the user presses F6.
F6 will perform any cleanup tasks, shut down the engine and save any necessary data if need be, dissertation cheat. Development for the detection functions will begin in stage 8. Carrying on from the BunnyHop development dissertation cheat covers a vast majority of the memory management class and code needed to attach the dissertation cheat hack to the Counterstrike process. Last year, Valve released an update that prevents wallhacks dissertation cheat as they used too, dissertation cheat.
There is no credible information for this update but the cheating community confirmed. As a side note, the offsets for Counterstrike have recently been changed due to a recent update, dissertation cheat.
So silently, I found them again using previous methods from other blog posts and updated the other hacks. I will be using the same reading and writing to memory WINAPI functions, ReadProcessMemory RPM and WriteProcessMemory WPM which allows the reading and writing to processes in memory. Below is the switch statement within the main functions which executes different cases depending upon which number the player types. To run the Radar hack, dissertation cheat, the player must enter the number 2 which will execute the code below that is commented.
The RadarHack was not a complicated cheat to code, however, due to recent dissertation cheat to the engines player states, I will demonstrate the effectiveness of this cheat and explain how this has affected the RadarHack. I will, however, be splitting up each hack into individual objects with their own headers and source files but for testing purposes, this is not necessary. The mini-map image on the bottom left is a rough image showing the players position and an enemies position with 5 players each side, dissertation cheat.
This was taken during the usage of the RadarHack which indicates that from the players positioning and the FOV value set by default, dissertation cheat, the game engine only allowed that single enemy to be drawn to the mini-map. As stated in the overview, dissertation cheat, this is due to the recent updates that prevent a full map coverage for the RadarHack.
To prevent any blatantly obvious invalid memory writes, dissertation cheat, I should really do some dormant checks. However, this is not crucial at this stage. The RadarHack is functional that functions as a short range radar with only players within the FOV and default distance being displayed. The image on the right is the RadarHack currently running after checking that the CSGO process exists and loading all the games modules before running the hack.
Now the helper class has been created; I can now begin the development on the actual BunnyHop Script. The helper class does most the work, but the actual hack class just uses the gathered data from the helper class to make small changes to data in the Counterstrike memory. This is a basic model for the ReadProcessMemory as stated on the MSDN along dissertation cheat other useful commented information.
This is a basic model for the WriteProcessMemory as indicated on the MSDN with informative comments relative to Counter-strike Source. I do not want the script to jump if the player is in the air. The scripts flow of execution will be programmed as shown in the flow chart. I have created dissertation cheat simple function that returns nothing but will be the logic for performing the jumps and when the script should jump. If you refer to the flowchart above, the code will follow that design, dissertation cheat.
If the BunnyHopStatus is true, then the script will proceed to an if-else statement block that writes to the Counter-strike memory. I think I have gathered all the information I need to create this simple bunny hop script. All the information will be recapped below for easy accessibility. Briefly looking over the information above, some of the information is not required since some of the information such as the distance between health and team number which was used correctly to identify the base entity address for the client.
The irrelevant information will be crossed out to avoid confusion. Before I can write any functional code that will utilize the information above, I need to write a helper script to find the Counter-strike process and set up some handles to the client, dissertation cheat.
Beginning from the top of my helper script, I will start with finding the Counter-strike process by taking a snapshot of all the active system processes then comparing each received process name with the specified Counter-strike process name, dissertation cheat. If the comparison is valid and the Counter-strike process is found within the system, dissertation cheat, the function will return the Counter-strike process ID for use in finding all the processes threads.
This step is crucial for my hack to work externally as I will be hooking into Counter-strikes occupied memory to read and write data.
The GetProcessThreads function follows the same structure as finding the processes with minor modifications. Firstly, all the checks that verify that the handles returned are valid same as the finding the process but the data used is slightly different. Secondly, the CreateToolHelp32Snapshot function receives a different parameter in comparison to finding the process. For example, to get all the process threads from a specific process, all the processes must have already been retrieved and checked, dissertation cheat.
After getting all the threads associated with the Counter-strike process, I will now be able to take a snapshot of all the modules by retrieving the base address for each module then load them all to check which one I need.
Expanding on the descriptions in the comments below, dissertation cheat, the GetModuleNameAddr function will take two parameters.
The first value being passed is the module name to find and the process ID of the application to be snapshotted. As in all the helper class functions, dissertation cheat, there are the integrity checks in place, such as to terminate the program if the snapshot is invalid.
My hack program process as it stands cannot perform any low-level actions on Counter-strike such as modifying memory or debug so I will slightly alter the access token privileges associated with my hack to allow these abilities. Firstly, dissertation cheat, I create two handles, one to the current process the hack and the other to the access token then open the process token by providing the handle to the current process and the access token.
Now I have already dissertation cheat access to adjust the token privileges; I will now set a few values before applying the adjustments such as the privilege count, dissertation cheat, the LUID and the attribute to enable.
With a majority of the helper class out of the way, dissertation cheat, all that is left is to create a simple function that encapsulates and calls all those functions to gather data. The required access right dissertation cheat be checked against the security descriptor for the process and be denied.
Dissertation cheat, the two functions are simple getters that are used in the main class to get the handle to the Counter-strike dissertation cheat and the client module. Following on from my last blog post, to recap, the information I have gathered from OllyDBG is as follows. The next information I need to get is the base dissertation cheat by using the information above. In-game, I have started a private game on Counter-strike with bots, dissertation cheat.
For this next step, I need to open the counter-strike process hl2, dissertation cheat. exe in Cheat Engine to be able to scan for different values, dissertation cheat. However, I will browse each addresses dissertation cheat region to search for the team number. If I recall correctly, the team address should be 8 bytes away from the health address.
Count the arrows to verify, dissertation cheat. This memory address is the direct dissertation cheat of the health value and will be able to give us the players base entity. The base entity could be dissertation cheat of those 4 remaining paths, now to find out which one is the base entity for the client, dissertation cheat, I will need to add the memory address manually. Then convert to hex and dissertation cheat the data structures within the memory to find the health value and team value by saving the structure then reading through it, dissertation cheat.
The path above is the correct address after dissecting the data structures, dissertation cheat. The last information I need to find is the function call memory address pointer for forcing the engine to jump.
Degrees For Sale: Inside The Essay Writing Industry: Students On The Edge
, time: 5:34Jill Biden’s Doctorate Is Garbage Because Her Dissertation Is Garbage

has become the best essay writer service after many years Dissertation Cheat of experience. Our company hires professional essay writers to help students around the world. Our skillful Dissertation Cheat essay writers supply writing and editing services for academic papers. Our subjective is to create an ideal paper to help you to succeed in your grades/10() It’s a good idea to make sure you are: Working in a study space that is well-laid out. Being honest with yourself and the people around you about how you are getting on. Working and referring to a clear plan for the overall project (with extra time included for anything unforeseen that may Eating Apr 11, · University dissertation project on developing a simple anti-cheat system with a custom client-sided cheat written in C++ using Visual Studio. Stage 8 – Detection Methods April 11, November 5, Craig Leave a comment

No comments:
Post a Comment